The data centre forms the backbone of every organisation’s IT ecosystem, supporting secure infrastructure, information security, and continuous operations. It manages vast volumes of critical data, making it a prime target for cyberattacks. A breach or successful intrusion can expose sensitive information, disrupt business processes, damage reputation, and result in long-term client loss. Strong data protection solutions and reliable privacy compliance measures are essential to maintain trust and safeguard business continuity.
CyberSec Consulting provides advanced cybersecurity and data privacy services designed to secure your most valuable digital assets. Our team of experienced security engineers and analysts delivers enterprise security solutions, risk mitigation strategies, cloud security controls, and comprehensive cyber defence mechanisms to protect your data across all environments.

Database Security
Database Security is a key pillar of modern IT security and cybersecurity. CyberSec Consulting implements proven tools, robust processes, and advanced
methodologies to secure databases and database management systems (DBMS). These capabilities protect core data assets, stored functions, applications,
servers, and associated network links from unauthorized access, insider threats, and malicious attacks.
Our database protection solutions enhance visibility, strengthen access controls, and support information security best practices across the organisation.
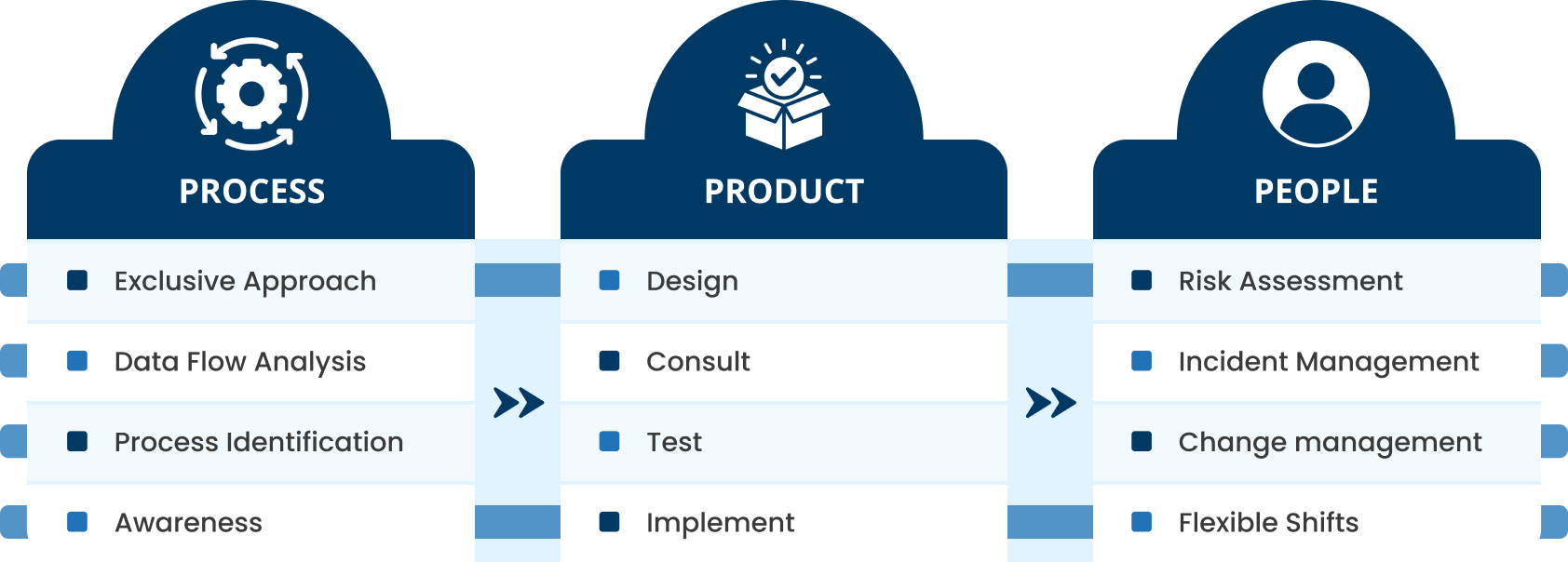
Data Security & Privacy Risks
Data has become the lifeblood of every organisation, driving digital transformation and business decisionmaking. As data volumes expand, so do the threats to data security and privacy. Organisations must adopt agile and scalable cybersecurity solutions to protect sensitive information from emerging risks, cyberattacks, insider misuse, and compliance violations.
CyberSec Consulting provides end-to-end Database Security and Data Protection services designed to secure data at rest, in use, and in transit. Our approach integrates data governance, security monitoring, threat prevention, and enterprise-grade protection to ensure continuous security across complex IT environments.
Data Protection Flow
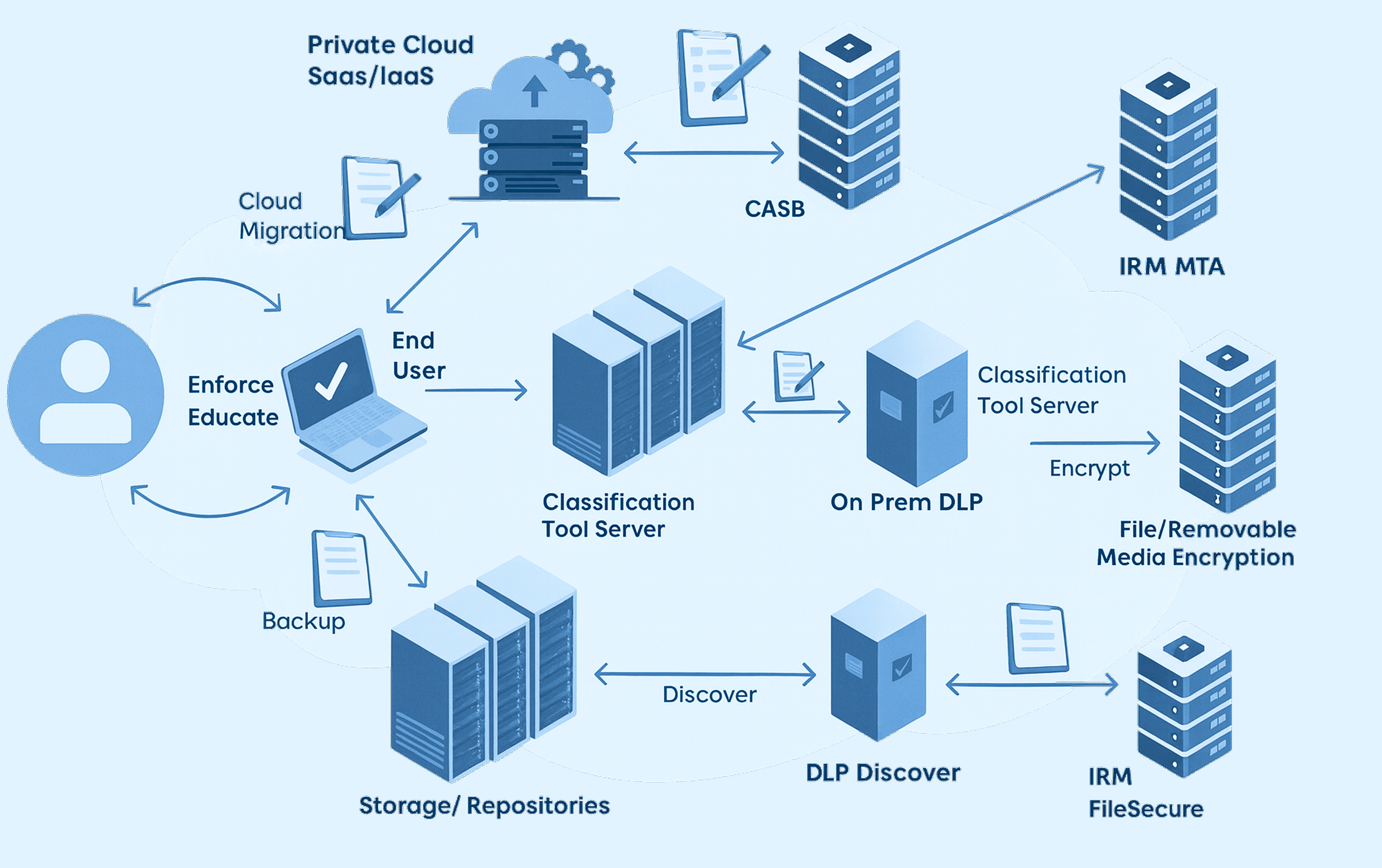
Data & Content Security Services
Data Classification
- Data classification forms the core of a strong data governance and cybersecurity framework.
- By identifying and categorizing information based on sensitivity, organisations gain better control over access management, compliance, and risk mitigation.
- CyberSec Consulting uses advanced automated tools to classify structured and unstructured data, ensuring stronger information security, privacy compliance, and enterprise-wide data protection.
Data Leakage Prevention (DLP)
- Data Leakage Prevention is essential in preventing unauthorized data movement, accidental exposure, or malicious exfiltration.
- Our security experts deploy advanced DLP tools and enterprise security controls that detect, block, and monitor risky behaviour across endpoints, networks, cloud platforms, and SaaS applications.
- These DLP solutions strengthen cyber defence, support IT security compliance, and protect sensitive business information from compromise.
Cloud DLP
- Cloud DLP protects sensitive data stored or shared across cloud services, SaaS platforms, and hybrid environments.
- It ensures secure cloud collaboration, prevents data misconfiguration risks, and supports cloud security best practices.
On-Premises DLP
- On-prem DLP provides deep visibility, real-time monitoring, and policy-based control over data within internal networks.
- It helps organisations enforce strict information security rules, prevent insider misuse, and secure sensitive data.
Digital Rights Management (DRM)
- Digital Rights Management safeguards sensitive documents and digital assets with strong encryption, access restrictions, and usage control.
- This ensures secure document handling and prevents unauthorized sharing, printing, or editing—even outside the organisation.
Zero Trust Security
- Zero Trust Security operates on the principle of “never trust, always verify.”
- Every user, device, and application must prove its legitimacy before gaining access to sensitive information.
- CyberSec Consulting implements Zero Trust architectures that reduce attack surfaces, prevent lateral movement, and enhance IT security across distributed environments.
FAQs
Database Security protects databases and DBMS from unauthorized access, cyberattacks, insider threats, and data breaches while ensuring information security and business continuity.
Data Classification identifies and categorizes sensitive data to improve access control, strengthen data governance, support privacy compliance, and reduce data security risks.
Data Leakage Prevention (DLP) monitors, detects, and blocks unauthorized data transfer across endpoints, networks, cloud platforms, and SaaS applications to prevent data exfiltration.
Cloud DLP secures data in cloud and SaaS environments, while On-Premises DLP protects internal systems, databases, and networks with real-time monitoring and policy enforcement.
Digital Rights Management (DRM) uses encryption and access controls to prevent unauthorized sharing, copying, editing, or printing of sensitive digital content.
Zero Trust Security enforces continuous verification for every user and device, reduces attack surfaces, prevents lateral movement, and strengthens enterprise cybersecurity posture.
Copyright © 2026 CyberSec Consulting – All Rights Reserved



.png
)



